Waircut Free Download
Waircut 2.0 is a powerful tool for auditing Wi-Fi security. It tests WPS vulnerabilities, performs PIN generation attacks, and provides detailed reports to enhance network protection.

Waircut, which stands for Wireless Air Cut, is a specialized tool designed to audit and test the security of Wi-Fi networks by identifying vulnerabilities in the Wi-Fi Protected Setup (WPS) protocol. Its user-friendly graphical interface and robust functionality make it an essential tool for network administrators and security enthusiasts alike. This tool not only helps in identifying potential security risks but also provides insights into how to fortify your network against potential threats.
Key Features
Real-time Testing
Waircut provides real-time feedback during testing, allowing users to see the progress.
Reaver Integration
Waircut often works in conjunction with Reaver, a command-line tool.
Compatibility
The tool is compatible with various wireless adapters and can be used.
(GUI)
Waircut comes with an easy-to-use graphical interface, making it accessible for users.
How Waircut Works
Waircut operates as a powerful tool for auditing and securing wireless networks by focusing on identifying and exploiting WPS (Wi-Fi Protected Setup) vulnerabilities. Here’s a detailed breakdown of how Waircut works
Process of Scanning for Available Wi-Fi Networks
- Initiation: When you start Waircut, the first step is to scan for all available Wi-Fi networks in the vicinity. This process involves the tool sending out probe requests and listening for responses from wireless access points.
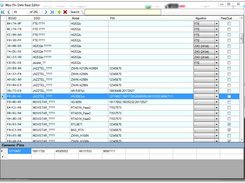
- Detection: Waircut detects these responses and compiles a list of available Wi-Fi networks, displaying essential details such as the SSID (network name), BSSID (MAC address of the access point), signal strength, and security protocols in use.
Identifying WPS-Enabled Networks
- WPS Detection: Among the detected networks, Waircut specifically identifies those that have WPS enabled. WPS is a feature designed to simplify the process of connecting devices to a Wi-Fi network, but it has known vulnerabilities that can be exploited.
- Filtering: The tool filters out networks that do not have WPS enabled, focusing only on those that do. This step is crucial as WPS-enabled networks are the primary targets for vulnerability testing with Waircut.
Step-by-Step Testing Process
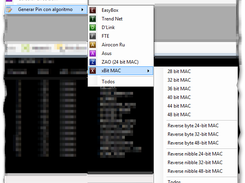
- Initiate Attack: Once a WPS-enabled network is identified, the user selects the target and initiates the WPS vulnerability test using either Reaver or Pixie Dust.
- Brute-Force or Exploit: For Reaver, the tool starts a brute-force attack, attempting various PIN combinations until the correct one is found. For Pixie Dust, the tool analyzes the network’s response to a WPS setup attempt to exploit weaknesses in the PIN generation process.
- Monitor Progress: Waircut provides real-time feedback on the progress of the attack, showing the status of attempts and any successful entries.
Generating and Understanding Reports
- Compiling Results: After completing the tests, Waircut compiles the results into a detailed report. This report includes information on the security status of the tested networks, indicating whether vulnerabilities were found and successfully exploited.
- Report Elements: The report typically contains the network’s SSID, BSSID, security protocol, WPS status, type of attack used, and the outcome of the tests.
Recommendations for Addressing Vulnerabilities
- Interpreting Findings: Users need to carefully review the report to understand the specific vulnerabilities identified in their networks. The findings will indicate whether the network’s WPS feature is compromised and how.
- Taking Action: Based on the report’s recommendations, users should take immediate steps to secure their networks. Common recommendations include disabling WPS, updating router firmware, and configuring strong, unique passwords.
- Ongoing Monitoring: Regularly auditing the network using tools like Waircut ensures that any new vulnerabilities are promptly identified and addressed, maintaining robust network security.
| Application Name | Details |
|---|---|
| File Size | 3 MB |
| Content Rating | 4+ |
| Supported Platforms | Microsoft Windows |
| Supported Version | Windows 10, 8, 7, Vista and XP |
| Category | Security Tool |
Step-by-Step Guide to Using Waircut
Using Waircut effectively involves several steps, from installation to generating detailed reports. Here’s a comprehensive guide to get you started:
Installing Waircut
Downloading and Setting Up the Tool:
- Visit the Official Website: Go to the official Waircut website or a trusted source to download the latest version of the tool.
- Download the Installer: Locate the download link for the installer and download it to your computer.
- Run the Installer: Once the download is complete, run the installer. Follow the on-screen instructions to install Waircut on your system.
Installation Prerequisites

- Operating System: Ensure your computer is running a compatible Windows operating system (Windows 7, 8, 10, etc.).
- Network Adapter: You need a compatible wireless network adapter that supports monitor mode and packet injection.
- Additional Tools: Some versions of Waircut may require additional tools or dependencies (e.g., Aircrack-ng suite, .NET Framework). Make sure these are installed before proceeding.
Initial Setup
Configuring Settings:
- Launch Waircut: Open the Waircut application from your desktop or start menu.
- Access Settings: Navigate to the settings menu. This is usually accessible from the main interface.
- Configure Preferences: Adjust settings according to your needs, such as language, network adapter selection, and scanning preferences.
Preparing for the First Scan:
- Select Network Adapter: Choose the appropriate network adapter from the list provided in the settings. Ensure it supports monitor mode.
- Enable Monitor Mode: If required, enable monitor mode for your network adapter. This allows Waircut to capture all wireless traffic in the vicinity.
- Verify Dependencies: Ensure all required dependencies and tools are installed and properly configured.
Performing a Network Scan
Initiating the Scan:
- Start Scanning: From the main interface, click on the “Scan” button to start scanning for available Wi-Fi networks.
- Monitor Progress: Waircut will display a list of detected networks along with relevant details like SSID, BSSID, signal strength, and security protocols.
Interpreting Scan Results:
- Review Network List: Analyze the list of detected networks. Look for networks with WPS enabled, as these are the primary targets for vulnerability testing.
- Filter Networks: Use filtering options to narrow down the list to WPS-enabled networks.
Testing for Vulnerabilities
Conducting WPS Vulnerability Tests:
- Select Target Network: Choose a WPS-enabled network from the scan results for vulnerability testing.
- Initiate WPS Test: Click on the “Test” button or similar option to start testing for WPS vulnerabilities using Reaver or Pixie Dust methods.
- Monitor Attack Progress: Waircut will attempt to exploit the WPS vulnerability. Monitor the progress and status updates provided by the tool.
Understanding Test Outcomes:
- Successful Exploits: If the test is successful, Waircut will display the WPS PIN and possibly the network password.
- Failed Attempts: If the test fails, the tool will provide information on why it failed and may suggest alternative methods or steps.
Legal and Ethical Considerations
Responsible Use of Waircut
Importance of Ethical Hacking:
- Definition: Ethical hacking involves using the same tools and techniques as malicious hackers but with the goal of identifying and fixing security vulnerabilities to protect networks and systems.
- Purpose: The primary goal is to enhance security by proactively finding and mitigating potential threats before they can be exploited by malicious actors.
- Professionalism: Ethical hackers operate within the bounds of the law and follow a strict code of ethics, ensuring that their actions do not harm individuals or organizations.
Legal Implications of Unauthorized Use:
- Illegality: Using Waircut or similar tools on networks without explicit permission is illegal and considered unauthorized access. This is a breach of laws designed to protect privacy and data security.
- Consequences: Unauthorized use can lead to severe legal consequences, including fines, imprisonment, and civil lawsuits. Additionally, it can damage one’s professional reputation and future career prospects.
- Ethical Breach: Beyond legal repercussions, unauthorized use is a breach of ethical standards. It undermines trust and can cause significant harm to individuals and organizations by compromising their network security.
Obtaining Permission
Ensuring Proper Authorization Before Testing:
- Written Consent: Before conducting any network audit or penetration test, it is essential to obtain written consent from the network owner or administrator. This consent should explicitly state the scope and objectives of the testing.
- Clear Communication: Communicate clearly with stakeholders about what the testing will involve, the potential risks, and the expected outcomes. Ensure that all parties understand and agree to the terms.
- Scope Definition: Define the scope of the testing to avoid unintended consequences. Specify which networks and systems are to be tested and what methods will be used.
Legal Guidelines and Best Practices:
- Compliance with Laws: Ensure that all actions comply with relevant local, national, and international laws. This includes data protection regulations, computer misuse laws, and privacy laws.
- Adhering to Industry Standards: Follow industry standards and best practices for ethical hacking and network security testing. This includes guidelines from organizations such as the EC-Council, Offensive Security, and the Information Systems Security Association (ISSA).
- Documentation and Reporting: Maintain thorough documentation of all activities performed during the testing. This includes the methods used, the findings, and the actions taken to address vulnerabilities. Provide detailed reports to stakeholders.
- Minimizing Impact: Conduct tests in a manner that minimizes the impact on the network and its users. Avoid causing disruption to business operations and ensure that any potential risks are mitigated.
- Continuous Education: Stay informed about the latest developments in network security and ethical hacking. Continuous education and certification help maintain a high standard of practice and adherence to ethical guidelines.

Yes, Waircut can automate scanning and testing processes.
Yes, Waircut can scan and test multiple networks in a single session.
Yes, Waircut generates detailed reports on the security status of each tested network.
Yes, Waircut allows you to export reports for further analysis and documentation.
Regular audits are recommended, at least quarterly or whenever significant changes are made to the network.
Restart Waircut and try scanning again. Ensure your system meets the requirements and that your Wi-Fi adapter is compatible.
Check if your Wi-Fi adapter is properly connected and supports monitor mode. Ensure WPS is enabled on nearby networks.
Waircut provides a detailed report of vulnerabilities found. Refer to the documentation for guidance on interpreting results.
No, Waircut identifies vulnerabilities, but fixing them requires manual intervention or additional tools.
The official Waircut website and user forums are good sources of information and support.
Ethical hacking helps identify and fix security vulnerabilities, protecting networks from malicious attacks.
Unauthorized use can lead to legal consequences, including fines and imprisonment.
Obtain written consent from the network owner or administrator before starting any tests.
Report the vulnerability to the network owner and provide recommendations for fixing it.
Open Waircut and click on the scan button to begin searching for available Wi-Fi networks.
Waircut can detect all Wi-Fi networks within range, including those with WPS enabled.
Waircut scans for networks and checks their settings to see if WPS is enabled.
WPS vulnerabilities are security flaws in the WPS protocol that can be exploited to gain unauthorized access to a network.
Reaver uses a brute-force method to guess the WPS PIN, while Pixie Dust exploits poor random number generation in WPS implementation.
The time varies depending on the network and the method used. Reaver can take hours, while Pixie Dust is usually quicker.
Download the installer from the official website and follow the installation instructions provided.
You may need to install additional software like the Reaver tool to fully utilize Waircut’s capabilities.
Yes, but it requires a compatible Wi-Fi adapter that can be connected to the virtual machine.
Yes, but it requires a compatible Wi-Fi adapter that can be connected to the virtual machine.
Waircut is primarily designed for Windows operating systems.
Waircut is designed for Windows, but some users may run it on macOS or Linux using compatibility layers or virtual machines.
Waircut - Free Download & Latest V2.0 For Window

Waircut - The Latest v2.0 for free. Secure your Wi-Fi with advanced WPS vulnerability checks and detailed network security reports. Download now!
Price: Free
Price Currency: $
Operating System: Windows 7, 8, 10 and Windows 11
Application Category: Software
4.9
